SSH, an acronym for Secure Shell, is a remote protocol that is widely used to make remote connections to servers, network devices, and other remote hosts that run the service. It uses a public/private key pair to encrypt traffic between the user and the remote host.
When making a connection, you might encounter the “ssh permission denied public key” error. In this guide, we seek to understand the cause of this error and how to address it.
Cause of SSH Permission denied (publickey) Error
The root cause of this error is mostly a misconfiguration in the /etc/ssh/sshd_config file which is the default SSH configuration file.
Another culprit is insufficient permissions on the authorized_keys file on the remote system. The file contains the public keys of client systems allowed to SSH into the server.
Without much ado, let us check out possible solutions to solve this error.
Enable Password Authentication
As earlier pointed out, one of the reasons attributed to this error is a misconfiguration of the /etc/ssh/sshd_config file. One of the wrong settings is the disabling of the password authentication feature. This can happen in case someone is using SSH Key-based authentication only and for some reason, the private key is not present.
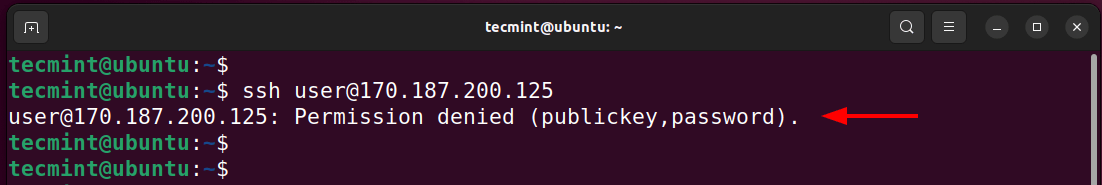
To address this error, edit the default SSH configuration file.
$ sudo vim /etc/ssh/sshd_config
Locate the PasswordAuthentication attribute and set it to yes as shown below.
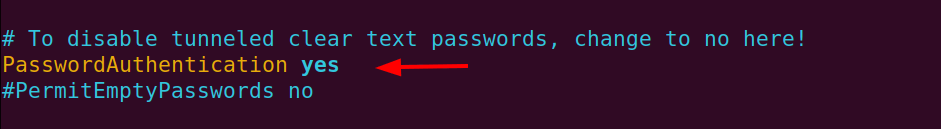
Save the changes and exit the configuration file. Then restart the SSH service for the changes to come into effect.
$ sudo systemctl restart sshd
You should now be able to connect seamlessly to the remote host.
Check SSH Authorized_keys Permission
Sometimes, the error comes from incorrect permissions and ownership of the ~/.ssh/authorized_keys file on the remote system.
The ~/.ssh/authorized_keys file is located on the remote server. It contains the public SSH key from the client system connecting to it using SSH-key authentication. Remember that the private key should remain on the client system and never be shared.
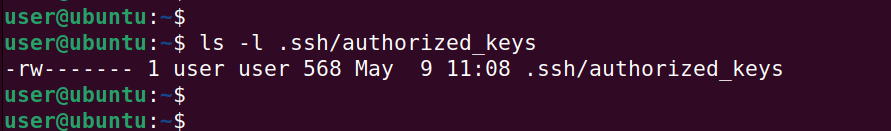
The authorized_keys file should be owned by the user on the remote system. In addition, the user should have read and write permissions.
If this is not the case, set the permissions to the file as shown.
$ sudo chmod 600 ~/.ssh/authorized_keys $ ls -l .ssh/authorized_keys
Back on the client system, ensure that Public and Private Keys have the correct permissions.
- The Private Key should have read and write permissions only for the file owner.
- The Public Key should have read and write permissions for the file owner and read permissions for both the group and other global users.
If this is not the case, configure the permissions as follows in octal format.
$ sudo chmod 600 ~/.ssh/id_rsa $ sudo chmod 644 ~/.ssh/id_rsa.pub
Those are the two main ways that you can use to troubleshoot the “ssh permission denied public key” error. Have we left something else out? Do let us know in the comment section.