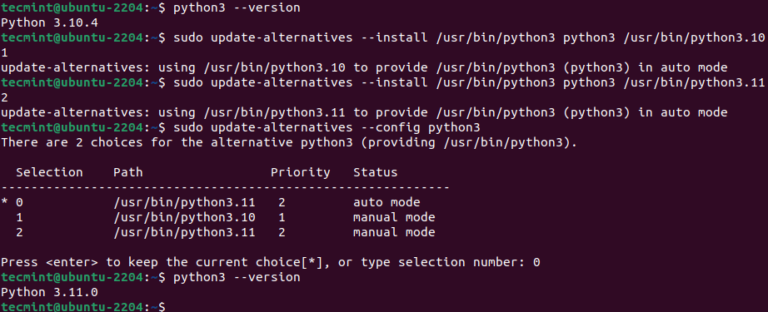
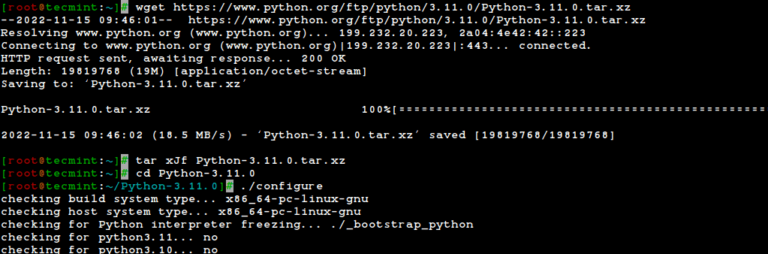
How to Install Latest Python Version in Ubuntu
Python is the fastest-growing major general-purpose programming language. There are a number of reasons attributed to this, such as its readability and flexibility, ease to learn and use, reliability, and efficiency as well. There are…