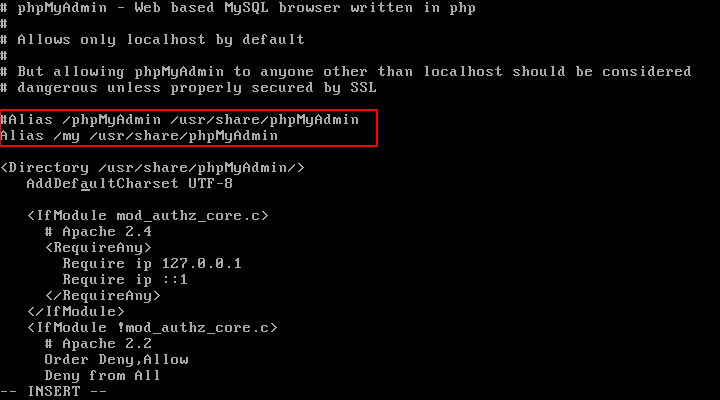
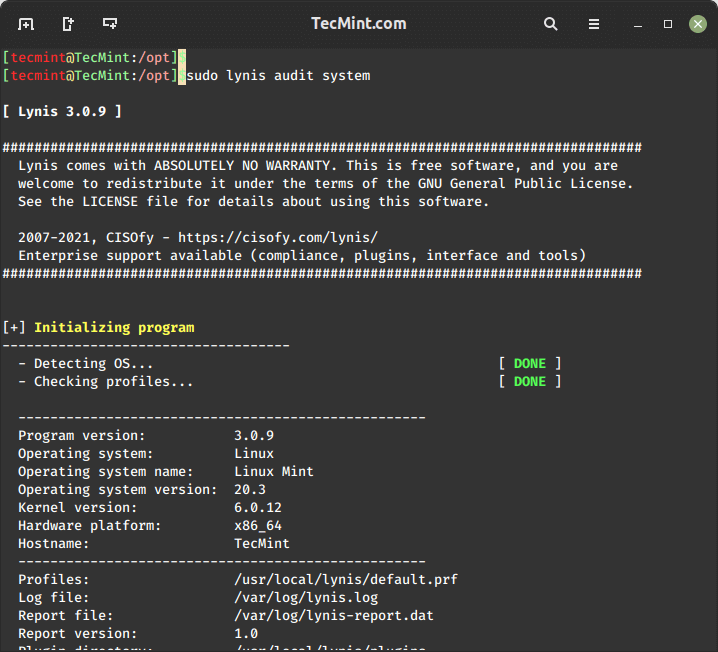
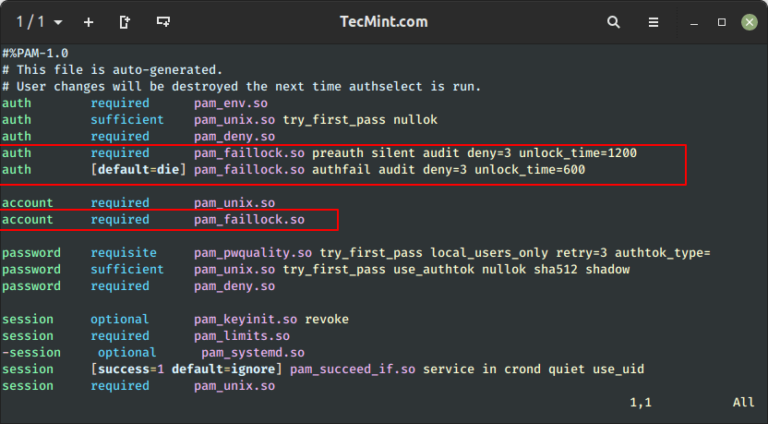
How to Stop and Disable Unwanted Services from Linux System
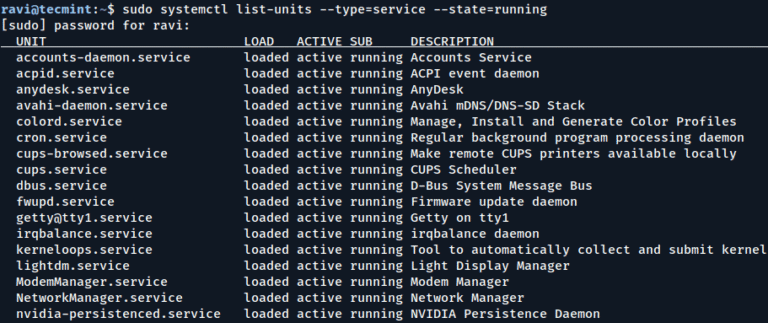
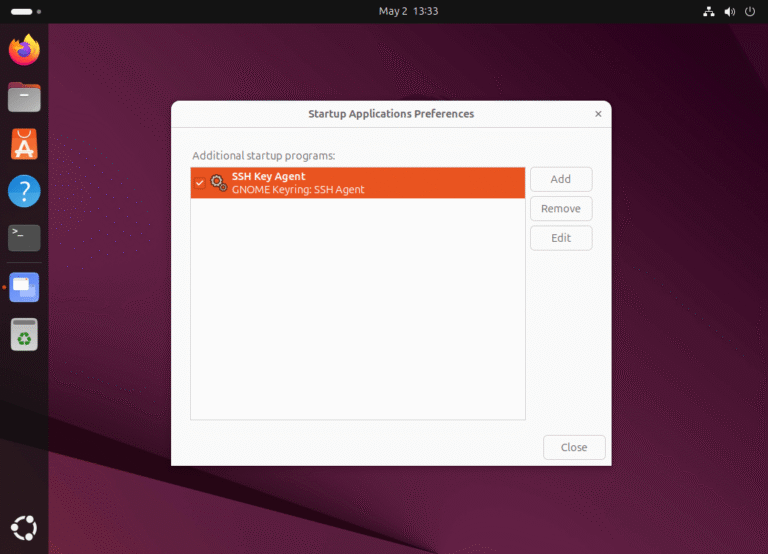
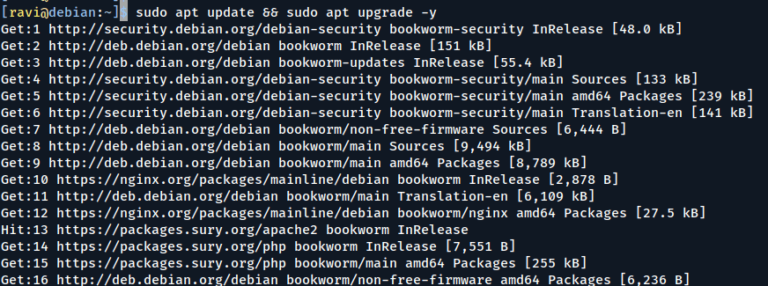
When you build a server according to your plan and requirements, you want it to run quickly and efficiently, right? But did you know that modern Linux systems, especially those using systemd, often install and…