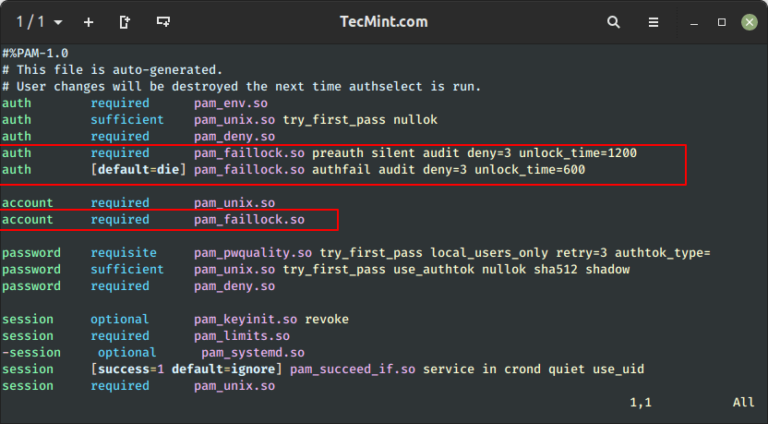
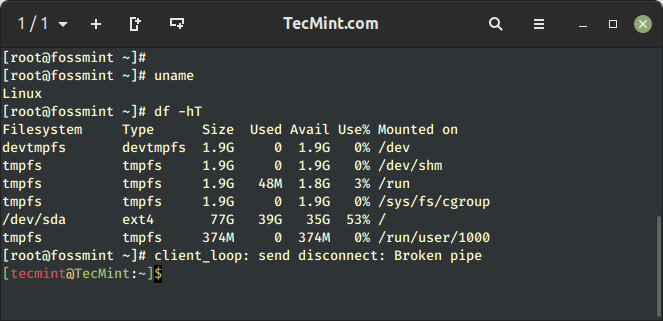
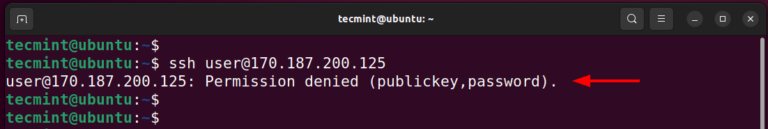
How to Setup SSH Passwordless Login in Linux [3 Easy Steps]
SSH (Secure SHELL) is an open-source and trusted network protocol that is used to log in to remote servers for the execution of commands and programs. It is also used to transfer files from one…