In my previous article, we learned the installation of Shorewall, configuration file setup, and the configuration of port forwarding over NAT. In this article, we will delve into common errors associated with Shorewall, provide solutions, and introduce its command line options.
Shorewall offers a wide array of commands that can be run on the command line. Having a look at the man shorewall should give you plenty to see, but the first task we are going to perform is a check on our configuration files.
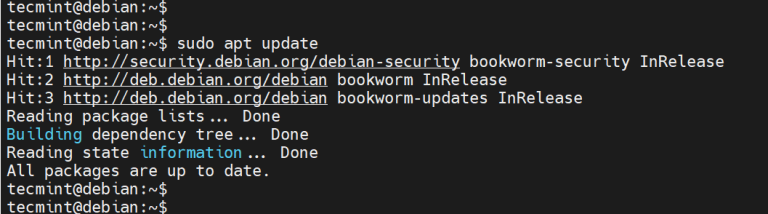
sudo shorewall check
Shorewall will print out a check of all of your configuration files, and the options contained within them.
The output will look something like this.
Determining Hosts in Zones... Locating Actions Files... Checking /usr/share/shorewall/action.Drop for chain Drop... Checking /usr/share/shorewall/action.Broadcast for chain Broadcast... Checking /usr/shrae/shorewall/action.Invalid for chain Invalid... Checking /usr/share/shorewall/action.NotSyn for chain NotSyn.. Checking /usr/share/shorewall/action.Reject for chain Reject... Checking /etc/shorewall/policy... Adding Anti-smurf Rules Adding rules for DHCP Checking TCP Flags filtering... Checking Kernel Route Filtering... Checking Martian Logging... Checking Accept Source Routing... Checking MAC Filtration -- Phase 1... Checking /etc/shorewall/rules... Checking /usr/share/shorewall/action.Invalid for chain %Invalid... Checking MAC Filtration -- Phase 2... Applying Policies... Checking /etc/shorewall/routestopped... Shorewall configuration verified
The magical line that we are looking for is the one at the bottom that reads: “Shorewall configuration verified”. If you receive any errors, they are most likely due to missing modules in your kernel configuration.
I will show you how to resolve two of the more common errors, but it behooves you to recompile your kernel with all of the necessary modules if you plan on using your machine as a firewall.
The first error, and most common, is the error about NAT.
Processing /etc/shorewall/shorewall.conf... Loading Modules... Checking /etc/shorewall/zones... Checking /etc/shorewall/interfaces... Determining Hosts in Zones... Locating Actions Files... Checking /usr/share/shorewall/action.Drop for chain Drop... Checking /usr/share/shorewall/action.Broadcast for chain Broadcast... Checking /usr/shrae/shorewall/action.Invalid for chain Invalid... Checking /usr/share/shorewall/action.NotSyn for chain NotSyn.. Checking /usr/share/shorewall/action.Reject for chain Reject... Checking /etc/shorewall/policy... Adding Anti-smurf Rules Adding rules for DHCP Checking TCP Flags filtering... Checking Kernel Route Filtering... Checking Martian Logging... Checking Accept Source Routing... Checking /etc/shorewall/masq... ERROR: a non-empty masq file requires NAT in your kernel and iptables /etc/shorewall/masq (line 15)
If you are seeing something resembling this, chances are that your current Kernel is not compiled with support for NAT. This is common with most out-of-the-box Kernels. Please read my tutorial on “How to compile a Debian Kernel” to get you started.
Another common error produced by the check is the error about iptables and logging.
shorewall check Checking... Processing /etc/shorewall/params... Processing /etc/shorewall/shorewall.conf Loading Modules.. ERROR: Log level INFO requires LOG Target in your kernel and iptables
This is also something you can compile into a new Kernel, but there is a quick fix for it if you’d like to use ULOG. ULOG is a different logging mechanism from syslog. It is pretty easy to use.
To set this, you have to change every instance of “info” to “ULOG” in all of your configuration files in /etc/shorewall. The following command can do that for you.
cd /etc/shorewall sudo sed –i ‘s/info/ULOG/g’ *
After that, edit the /etc/shorewall/shorewall.conf file and set the line.
LOGFILE=
To where you would like your log to be stored. Mine is in /var/log/shorewall.log.
LOGFILE=/var/log/shorewall.log
Running the following command again should give you a clean bill of health.
shorewall check
Shorewall’s command line interface comes with many handy one-liners for systems administrators. One frequently used command, especially when numerous changes are being made to the firewall, is to save the current configuration state so that you can roll back if there are any complications.
The syntax for this is simple.
sudo shorewall save <filename>
Rolling back is just as easy:
sudo shorewall restore <filename>
Shorewall can also be started and configured to use an alternate configuration directory. You can specify this is the start command, but you will want to check it first.
sudo shorewall check <config-directory>
If you simply want to try out the configuration, and if it is working, start it up, you can specify the try option.
sudo shorewall try <config-directory> [ ]
Shorewall is just one of many robust firewall solutions that are available on Linux systems. No matter what end of the networking spectrum you find yourself on, many find it to be simple and useful.
This is but a small start, and one that can get you on your way without going too heavily into networking concepts. As always, please research and have a look at the man pages and other resources. Shorewall’s mailing list is an awesome place and is up-to-date and well-maintained.