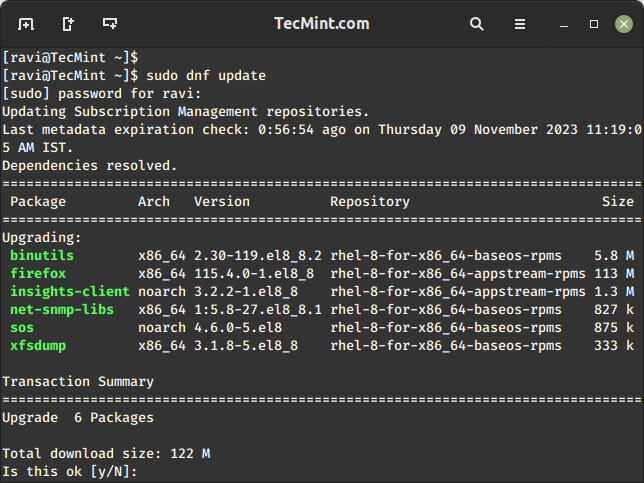
A stunning news from Rips Technologies, a remote code execution vulnerability has been detected in WordPress which is not an overnight issue but was unveiled for 6 years. WordPress has patched the issue partially as no other user’s site will face any kind of problem due to this vulnerability. It clearly does not mean that they can keep using the older versions of WordPress however using the latest version is the best method to ensure the safety of the site.
Due to this, a hacker can grab the author privileges with the access to login credentials of the users. It can lead to the execution of the PHP code with which they can run the whole control to the server or the site with which ruining the reputation is quite an effortless task to do. So, the execution of the desiring commands of the hackers can be achieved with this vulnerability.
The researchers also published a video demonstration of how the attack works which is shown below:
[embedded content]
Who gets affected?
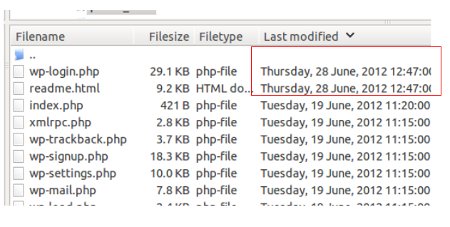
Not all the WordPress users were facing the issue but only those sites have the chances to get corrupted which have some authors as the hackers can get access to author privileges only. Also, the users which are still using the lower version of WordPress than version 4.9.9 and 5.0 can get affected by this.
Advancements by WordPress:
The latest WordPress Gutenberg has achieved success in saving the sites as well as the server from the hackers as the latest versions of WordPress 5.0.1, 5.1, 4.9.9 averted the utilization of the flaw. WordPress has restricted the unauthorized users in setting the Post Meta entries.
But, the Path Traversal issue is still unresolved but the WordPress technical experts are working on it.
Note: Now, If a WordPress user wants to secure their site from their vulnerability, then they should not install a plugin that allows the Post Meta entries to overwrite.